Me an my friend both have an Asustor NAS. We have both installed Duplicati from the NAS AppStore and created jobs that backup the data via SFTP to each others NAS. Of course we have also configured everything required around that like DNS entries, firewall ports etc. and it has been running for many months now without any issues.
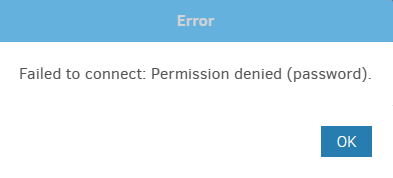
A few days ago we got the notification on our NAS that the new patch 4.2.5.RN33 is available. We both installed it and after the restart the backups were no longer working. The error message in Duplicati is “An established connection was aborted by the server.” Nothing else in our setup has changed, smoke tests show no issues with anything around it (IP is correct, ports are open etc.) and we both have the exact same problem after the exact same action (patch installation) so I clearly assume that this patch is the cause of the problem.
I checked the changelog but couldn’t really see anything suspicious (Release Notes - ASUSTOR NAS). Or could it be related to the OpenSSH fix?
I feel the new patch is changing (fixing) the behavior of the SFTP server in such a way that Duplicati can no longer communicate with it. So from my understabding a fix could be required either on the NAS or on Duplicati side.
Anybody else is observing this problem? How to analyze / drill down / fix this?
Disclaimer: I have created a similar issue in the Asustor forum: ASUSTOR Community Forum • View topic - SFTP no longer working after patch 4.2.5.RN33