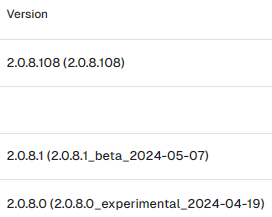
As announced in the latest canary/experimental/beta, the plan is to move to .NET8 builds going forward.
For those that want to help out or try the very latest, I have prepared a set of builds that use the .NET8 build & package process.
I hope (again) that this will be the last debug build and that we will be able to release canary builds going forward.
This build has a these fixes reported on the previous build:
- Suppressing Avalonia log messages
- Fixed error on Windows decrypting database
- Fixed issues with Docker images
The packages are signed (Windows + MacOS) and the GPG signatures are included.
Upgrade notice
Since RC4 encryption is no longer part of the open-source SQLite libraries, the builds will detect and remove the RC4 encryption before connecting to the database. If your security setup previously depended on this feature, make sure to adjust.
The file naming structure:
The filenames are named after operating system, chip architecture and intended use, e.g. linux-x64-gui.
The -gui builds also include the -cli executable, but are generally bigger due to the UI libraries.
The suffix denotes the installer type:
.zip: Generally just the files, zipped..deb: Debian package.rpm: RPM package.pkg,.dmg: MacOS packages.msi: Windows Installer
Docker images:
Docker images are pushed with the tags 2.0.8.108 and Debug.
List of images
duplicati-2.0.8.108_debug_2024-05-08-linux-arm64-cli.debduplicati-2.0.8.108_debug_2024-05-08-linux-arm64-cli.rpmduplicati-2.0.8.108_debug_2024-05-08-linux-arm64-gui.debduplicati-2.0.8.108_debug_2024-05-08-linux-arm64-gui.rpmduplicati-2.0.8.108_debug_2024-05-08-linux-arm64-gui.zipduplicati-2.0.8.108_debug_2024-05-08-linux-x64-cli.debduplicati-2.0.8.108_debug_2024-05-08-linux-x64-cli.rpmduplicati-2.0.8.108_debug_2024-05-08-linux-x64-gui.debduplicati-2.0.8.108_debug_2024-05-08-linux-x64-gui.rpmduplicati-2.0.8.108_debug_2024-05-08-linux-x64-gui.zipduplicati-2.0.8.108_debug_2024-05-08-osx-arm64-gui.dmgduplicati-2.0.8.108_debug_2024-05-08-osx-arm64-gui.pkgduplicati-2.0.8.108_debug_2024-05-08-osx-x64-gui.dmgduplicati-2.0.8.108_debug_2024-05-08-osx-x64-gui.pkgduplicati-2.0.8.108_debug_2024-05-08-win-arm64-gui.zipduplicati-2.0.8.108_debug_2024-05-08-win-x64-gui.msiduplicati-2.0.8.108_debug_2024-05-08-win-x64-gui.zipduplicati-2.0.8.108_debug_2024-05-08-win-x86-gui.msiduplicati-2.0.8.108_debug_2024-05-08-win-x86-gui.zipduplicati-2.0.8.108_debug_2024-05-08.signatures.zip