I dug up that the default hash is sha256. In order to reduce the chance of collisions, I’d like to use SHA512.
Can I change the hash used for a backup set that has already been backing up without breaking things (in other words, can the system deal with some blocks hashed sha256 and other blocks hashed sha512)?
Or am I better of clearing out my current backups and starting fresh?
Thanks.
Unfortunately, hash (like passphrase and blocksize) is one of the settings that can’t be changed once a backup has been created.
If you try to run a backup in which the --blockhash has been changed from it’s original value, you’ll get something similar the message below.
Note that there is a tool that can let you do things like change the passphrase (by downloading, re-encrypting, re-uploading EVERY file) but I doubt they’ll be able to do a blockhash change.
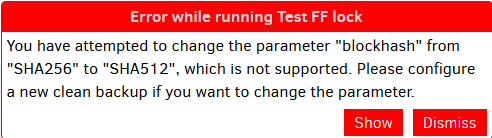
No sha256 collisions have been found yet. If you find one you can make money on it but you never ever will. Is that a lose win?
Don’t worry about it 
True. But they’ve broken SHA1 - they managed to change a document without changing its hash.
Of course SHA1 is “only” 160 bits… 
You should be able to use an adapted version of the python reencrypt script. Currently it does not support changing hash but that is only a small change to be made. You will need to change the manifest files as well I think.
Or not… The script doesn’t go deep enough.
You have to remember that SHA256 is not 1.6 times more complex than SHA1.
SHA256 is 40 thousand billion billion billion times more complex.
You can fit all the options of SHA1 inside SHA265 4… followed by 31 zeroes… times.
Breaking SHA1 isn’t easy, and to break SHA256 you have to do something so complex that it makes SHA1 look unfathomably insignificant.

Yes, I’m aware. It’s also not just size, but complexity of SHA2 vs SHA1. 
1 Like
Alright 
I don’t think you’ll be able to do anything but configure a new backup set.
As @Wim_Jansen points out the reencrypt script does not go deeply enough to do this.
I don’t even think it’s possible without, in effect, restoring all the data and backing it up again which would likely take much longer and require a complex new feature in the system.
1 Like




