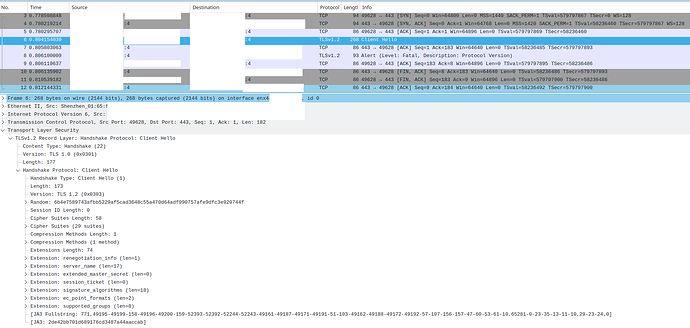
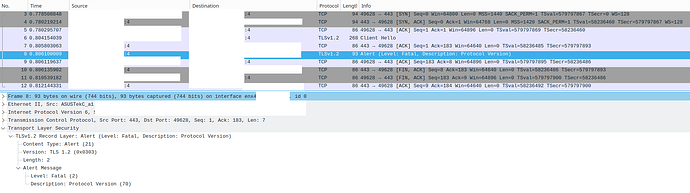
Hi. I have a backup to a WebDAV server (NextCloud 26.0.2 on YunoHost (Debian)) that had been working for a long time and stopped working 2 days ago. Now I can’t connect to my WebDAV server; when I “Test connection”, I get the following exception (running Duplicati from the CLI):
Ssl error:1000042e:SSL routines:OPENSSL_internal:TLSV1_ALERT_PROTOCOL_VERSION
System.Net.WebException: Error: SecureChannelFailure (Authentication failed, see inner exception.) —> System.Security.Authentication.AuthenticationException: Authentication failed, see inner exception. —> Mono.Btls.MonoBtlsException: Ssl error:1000042e:SSL routines:OPENSSL_internal:TLSV1_ALERT_PROTOCOL_VERSION
at ./external/boringssl/ssl/tls_record.c:462
at Mono.Btls.MonoBtlsContext.ProcessHandshake () [0x00064] in :0
at Mono.Net.Security.MobileAuthenticatedStream.ProcessHandshake (Mono.Net.Security.AsyncOperationStatus status, System.Boolean renegotiate) [0x00106] in :0
at (wrapper remoting-invoke-with-check) Mono.Net.Security.MobileAuthenticatedStream.ProcessHandshake(Mono.Net.Security.AsyncOperationStatus,bool)
at Mono.Net.Security.AsyncHandshakeRequest.Run (Mono.Net.Security.AsyncOperationStatus status) [0x00006] in :0
at Mono.Net.Security.AsyncProtocolRequest.ProcessOperation (System.Threading.CancellationToken cancellationToken) [0x0012a] in :0
— End of inner exception stack trace —
at Mono.Net.Security.MobileAuthenticatedStream.ProcessAuthentication (System.Boolean runSynchronously, Mono.Net.Security.MonoSslAuthenticationOptions options, System.Threading.CancellationToken cancellationToken) [0x00346] in :0
at Mono.Net.Security.MonoTlsStream.CreateStream (System.Net.WebConnectionTunnel tunnel, System.Threading.CancellationToken cancellationToken) [0x001f4] in :0
at System.Net.WebConnection.CreateStream (System.Net.WebOperation operation, System.Boolean reused, System.Threading.CancellationToken cancellationToken) [0x001f5] in :0
— End of inner exception stack trace —
at System.Net.WebConnection.CreateStream (System.Net.WebOperation operation, System.Boolean reused, System.Threading.CancellationToken cancellationToken) [0x00275] in :0
at System.Net.WebConnection.InitConnection (System.Net.WebOperation operation, System.Threading.CancellationToken cancellationToken) [0x0015b] in :0
at System.Net.WebOperation.Run () [0x000b7] in :0
at System.Net.WebCompletionSource1[T].WaitForCompletion () [0x000b1] in <a85c1a570f9a4f9f9c3d2cfa5504e34f>:0 at System.Net.HttpWebRequest.RunWithTimeoutWorker[T] (System.Threading.Tasks.Task1[TResult] workerTask, System.Int32 timeout, System.Action abort, System.Func`1[TResult] aborted, System.Threading.CancellationTokenSource cts) [0x00118] in :0
at Duplicati.Library.Utility.AsyncHttpRequest+AsyncWrapper.GetResponseOrStream () [0x0004d] in :0
at Duplicati.Library.Utility.AsyncHttpRequest.GetRequestStream (System.Int64 contentlength) [0x00068] in :0
at Duplicati.Library.Backend.WEBDAV.ListWithouExceptionCatch () [0x0004a] in <1aa1326b13664b9f92f75d7048721a2d>:0
at Duplicati.Library.Backend.WEBDAV.List () [0x000a5] in <1aa1326b13664b9f92f75d7048721a2d>:0
at Duplicati.Library.Backend.WEBDAV.Test () [0x00000] in <1aa1326b13664b9f92f75d7048721a2d>:0
at Duplicati.Server.WebServer.RESTMethods.RemoteOperation.TestConnection (System.String url, Duplicati.Server.WebServer.RESTMethods.RequestInfo info) [0x000b7] in <30a34d71126b48248d040dda634ddad9>:0
at Duplicati.Server.WebServer.RESTMethods.RemoteOperation.POST (System.String key, Duplicati.Server.WebServer.RESTMethods.RequestInfo info) [0x00091] in <30a34d71126b48248d040dda634ddad9>:0
at Duplicati.Server.WebServer.RESTHandler.DoProcess (Duplicati.Server.WebServer.RESTMethods.RequestInfo info, System.String method, System.String module, System.String key) [0x00289] in <30a34d71126b48248d040dda634ddad9>:0
However, I can still browse my WebDAV with a regular client (Dolphin file manager).
I first thought that this would be because I had just changed my server’s TLS compatibility settings to Modern.[1][2] However, after switching them back to Intermediate (and rebooting my server), nothing changed. I tried toying with allowed-ssl-versions, to no avail.
I updated to Duplicati - 2.0.7.1_beta_2023-05-25, on Linux (Kubuntu LTS).
What can I do?