I have a backup job going to S3. When setting up the job from scratch, I followed this basic process:
- Walked through creating a new backup job in Duplicati
- Selected S3 as the destination
- Generated a GUID for my bucket name
- On AWS, created a new dedicated user for duplicati
- In duplicati did the “Generate IAM Policy” button and copied the results
- Created a new IAM policy in AWS and pasted what Duplicati gave me (I think I had to add “CreateBucket” as well to the default generated one
- Attached this policy to the new user I created, then added this user’s credentials to the backup config
At this point I tested the config and it passed successfully.
My backups are now completing, and the bucket was created in S3. From what I can tell, everything is working as it should. Files are being updated in the bucket, and I was able to do a test restore of a file successfully.
But on my S3 Management Console, it shows this under the “Access” column for the bucket:
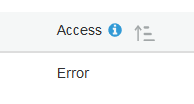
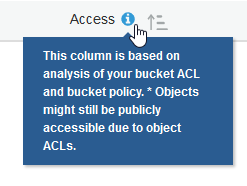
I just wanted to recount my steps and see if I missed something, or if anyone knows if I should be concerned about it or not. I don’t have a lot of AWS experience, and everything about the backup appears to be working fine. Was the IAM policy supposed to be put somewhere else instead of attached to a dedicated backup user? There doesn’t seem to be an actual problem, so is it safe to ignore it?
Thanks!
No, it is supposed to be attached to the user that is then granted access to the bucket. If you did not put any permissions on the bucket, it should not be publicly accessible AFAIK.
Not sure why it says Error but could it be because the IAM policy does not allow the user to query something on the bucket? Or because the policy scanner cannot understand the IAM policy?
I’m wondering if the “error” is due to your first comment - my user has access to the bucket but maybe external scanners or the bucket itself doesn’t have any accesses attached? The permissions tab for the bucket lists no public access for anyone.
Here’s the IAM policy attached to the user I have setup:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:CreateBucket",
"s3:ListBucket",
"s3:DeleteObject"
],
"Resource": [
"arn:aws:s3:::[my bucket]/*",
"arn:aws:s3:::[my bucket]"
]
}
]
}
In your IAM policy permission, you have to add following permission for S3 console to list all your buckets properly (without error).
{ "Version": "2012-10-17", "Statement": [ { "Sid": "Console_List_S3_Buckets", "Effect": "Allow", "Action": [ "s3:GetBucketLocation", "s3:ListAllMyBuckets", "s3:GetAccountPublicAccessBlock", "s3:GetBucketAcl", "s3:GetBucketPolicyStatus", "s3:GetBucketPublicAccessBlock" ], "Resource": "*" } }

