I am running Duplicati inside a docker container using this docker-compose.yaml:
version: '3'
services:
duplicati:
image: duplicati/duplicati
container_name: duplicati
environment:
- PUID=1000
- PGID=1000
- TZ=Europe/London
- CLI_ARGS= #optional
volumes:
- /datavol/duplicati:/config
- /mnt/backup/duplicati:/backups
- /datavol:/source/datavol
- /home/lukics:/source/home
ports:
- 8200:8200
restart: unless-stopped
user lukics has the ID 1000
when I backup this folder content:
-rw-rw-rw- 1 lukics lukics 173 Feb 3 13:45 printer_data/config/KlipperScreen.conf
-rw-rw-rw- 1 lukics lukics 51 Feb 2 06:33 printer_data/config/README.md
-rw-rw-rw- 1 lukics lukics 1938 Jan 26 16:17 printer_data/config/crowsnest.conf
lrwxrwxrwx 1 lukics lukics 41 Sep 22 02:24 printer_data/config/mainsail.cfg -> /home/lukics/mainsail-config/mainsail.cfg
-rw-rw-rw- 1 lukics lukics 2466 Jan 26 16:19 printer_data/config/moonraker.conf
-rw-r--r-- 1 lukics lukics 7733 Feb 4 14:58 printer_data/config/printer.cfg
-rw-rw-rw- 1 lukics lukics 770 Dec 31 15:34 printer_data/config/sonar.conf
-rw-r--r-- 1 lukics lukics 0 Feb 4 18:10 printer_data/config/test.cfg
-rw-r--r-- 1 lukics lukics 0 Feb 4 18:20 printer_data/config/test2.cfg
-rw-r--r-- 1 lukics lukics 0 Feb 4 18:28 printer_data/config/test3.cfg
lrwxrwxrwx 1 lukics lukics 60 Sep 22 02:24 printer_data/config/timelapse.cfg -> /home/lukics/moonraker-timelapse/klipper_macro/timelapse.cfg
and restore it to a different location I get this result:
-rw-r--r-- 1 root root 173 Feb 3 13:45 KlipperScreen.conf
-rw-r--r-- 1 root root 51 Feb 2 06:33 README.md
-rw-r--r-- 1 root root 1938 Jan 26 16:17 crowsnest.conf
drwxr-xr-x 2 root root 4096 Feb 4 16:27 macros
lrwxrwxrwx 1 root root 41 Feb 4 18:31 mainsail.cfg -> /home/lukics/mainsail-config/mainsail.cfg
-rw-r--r-- 1 root root 2466 Jan 26 16:19 moonraker.conf
-r--r--r-- 1 root root 7733 Feb 4 14:58 printer.cfg
drwxr-xr-x 2 root root 4096 Feb 1 22:44 printerconfig
-rw-r--r-- 1 root root 770 Dec 31 15:34 sonar.conf
-r--r--r-- 1 root root 0 Feb 4 18:10 test.cfg
-r--r--r-- 1 root root 0 Feb 4 18:20 test2.cfg
-r--r--r-- 1 root root 0 Feb 4 18:28 test3.cfg
lrwxrwxrwx 1 root root 60 Feb 4 18:31 timelapse.cfg -> /home/lukics/moonraker-timelapse/klipper_macro/timelapse.cfg
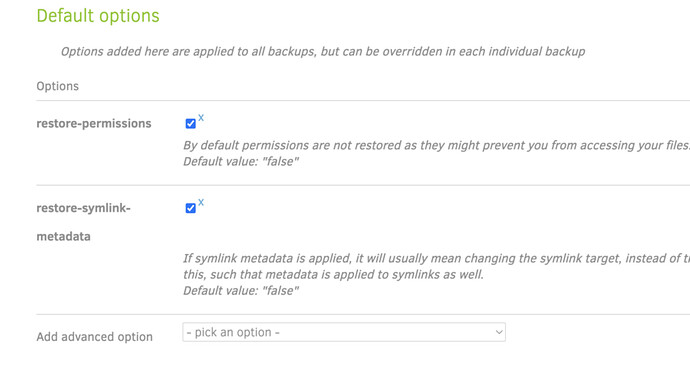
I have set options:
I would expect that the restored files have the same ownership as the source files.
Am I missing the point?