The OAuth handler was written 9 years ago, using the common Python 2.7 and is hosted on Google App Engine. Many things have changed since then, notably the deprecation of Python 2.x, which is now enforced on GAE.
There has been requests for a more closely guarded “in-house” hosting option, so instead of simply upgrading the Python solution, I have written a replacement service:
The new service is written in C# to cater better to the expertise of the development community around Duplicati and is built to be deployed in a Docker setup, with environment configuration.
I am currently hosting a functioning deployment for evaluation:
https://oauth-service.duplicati.com
The idea is that this service will eventually replace the GAE version, but it may not be as smooth a transition as I have hoped.
Known issues
Below is a list of know issues with the transition.
Missing providers
I have removed the providers that are no longer active, I do not expect this to cause any problems.
Windows Live & Microsoft Graph
Since 2020 there has been a requirement that the company is approved before it can offer the login functionality currently available from the GAE service. Duplicati has been allowed to operate but since I need to change the server, I cannot re-use the current tokens without interrupting service from the existing users.
I think the right solution is to register for a verified Microsoft Partner account and then discontinue the GAE version. This is something that takes some time and it also means that any MS based users will need to re-create their token.
Until I get the verified account, I have disabled the MS OAuth options on the hosted service.
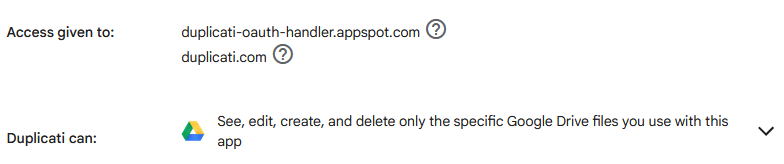
Google Drive
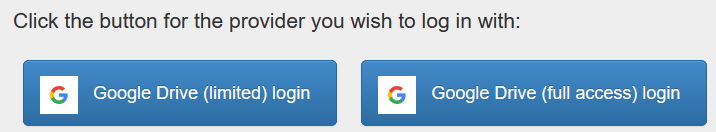
Google attempts to prevent unwanted exposure of sensitive files on Google Drive, with a limited access scope. Unfortunately, this method is designed for web-based applications that needs to store files for a particular app. This means that the app can only access the files it creates itself. Unfortunately, any access to the files from within Google Drive will render them unaccessible for the application, with no meaningful way to let the application re-own them.
For users changing the OAuth method, Google treats it as a new application, meaning there will no longer be access to files uploaded with the previous OAuth server, and no meaningful way to change ownership.
This leaves the full access method which Google is severely restricting and may not be permitting for Duplicati going forward. I have applied for access, and the initial review appears to be pending.
Summary
Despite the hassles this is a needed upgrade, caused by my choice of GAE many years ago.
If you have any input to the transition, ideas, hints, suggestions, questions, then please post them here.
At some point, when the transition path is clear, I think we can add a warning to all backups that are using the GAE OAuth server and then shut down the GAE service after a grace period.