Analyzing Crash Dumps / Blue Screens (BSoD) suggests WinDbg as a next step. I installed from Microsoft Store as mentioned by WinDbg in Wikipedia. It’s easier, but I don’t know any downside.
WinDbg Crash Analyzer - Find Root Cause of Windows Blue Screen / Green Screen
helped me a bit with figuring out how to drive this. The way the UI worked seems unconventional.
PROCESS_NAME: Duplicati.GUI.TrayIcon.exe is there, but I don’t know how it derives that. A process being involved at time of BSOD doesn’t seem like it means the process did anything bad.
STACK_TEXT:
ffffef8d`5e27eeb8 fffff801`79e45bcf : 00000000`00000050 ffffef8d`5e280008 00000000`00000000 ffffef8d`5e27f160 : nt!KeBugCheckEx
ffffef8d`5e27eec0 fffff801`79c38cd0 : ffffba01`b63d6568 00000000`00000000 ffffef8d`5e27f1e0 00000000`00000000 : nt!MiSystemFault+0x1ce12f
ffffef8d`5e27efc0 fffff801`79e0e86d : ffffef8d`5e27f1b0 fffff801`75575f7a ffffef8d`5e27f200 00000000`0000000d : nt!MmAccessFault+0x400
ffffef8d`5e27f160 fffff801`7a1233d0 : 00000000`00000000 00000000`00000038 fffff801`76273000 fffff801`755ab527 : nt!KiPageFault+0x36d
ffffef8d`5e27f2f0 fffff801`762b54ab : ffffca88`6ef38570 00000000`00000000 00000000`00000000 00000000`00000000 : nt!FsRtlQueryCachedVdl+0x100
ffffef8d`5e27f3e0 fffff801`755764cb : 00000000`00000000 00000000`00000000 ffffba01`00000000 ffffba01`b60132e0 : WdFilter!MpPreCleanup+0xf3b
ffffef8d`5e27f5e0 fffff801`75575f7a : ffffef8d`5e27f800 00000000`00000012 ffffba01`d131d200 00000000`00000000 : FLTMGR!FltpPerformPreCallbacksWorker+0x36b
ffffef8d`5e27f700 fffff801`75575021 : ffffef8d`5e280000 ffffef8d`5e279000 ffffba01`cd6d1a20 ffffef8d`5e27f810 : FLTMGR!FltpPassThroughInternal+0xca
ffffef8d`5e27f750 fffff801`75574a2b : ffffffff`fffe7960 00000000`00000000 00000000`00000000 ffffba01`c7899200 : FLTMGR!FltpPassThrough+0x541
ffffef8d`5e27f7e0 fffff801`79c4a295 : ffffba01`d131d2b0 fffff801`79c4a15d 00000000`00000000 00000000`00000000 : FLTMGR!FltpDispatch+0x8b
ffffef8d`5e27f840 fffff801`7a030277 : 00000000`00000001 ffffba01`d131d2b0 00000000`00000000 00000000`00043002 : nt!IofCallDriver+0x55
ffffef8d`5e27f880 fffff801`7a03831f : ffffba01`c7899200 00000000`00000001 ffffca88`00000000 ffffba01`d131d280 : nt!IopCloseFile+0x177
ffffef8d`5e27f910 fffff801`7a03320c : 00000000`00000f88 00000000`00000000 ffffba01`c093c080 fffff801`7a0f3910 : nt!ObCloseHandleTableEntry+0x51f
ffffef8d`5e27fa50 fffff801`79e12708 : ffffba01`c093c000 ffffba01`c8faffe0 ffffef8d`5e27fb40 ffffef8d`5e27fb40 : nt!NtClose+0xec
ffffef8d`5e27fac0 00007ff8`6cd0d6d4 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
00000013`7ab7ee78 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ff8`6cd0d6d4
SYMBOL_NAME: WdFilter!MpPreCleanup+f3b
MODULE_NAME: WdFilter
IMAGE_NAME: WdFilter.sys
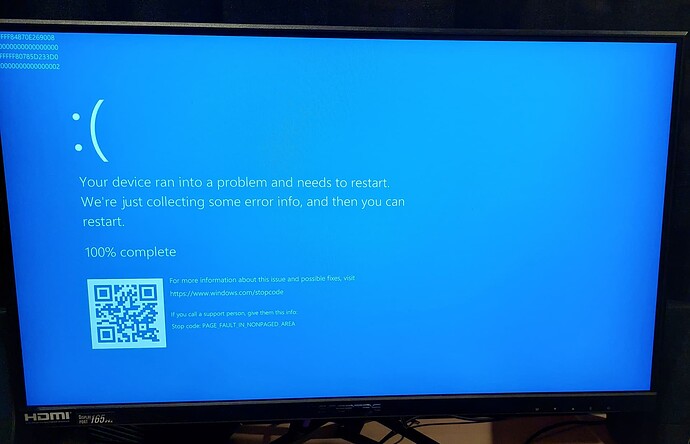
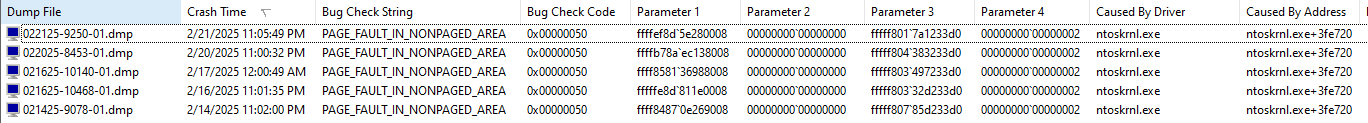
Looks (guessing a lot because I don’t do Windows internals) a file was closed, and Windows Defender did something it shouldn’t have done, thereby causing the BSOD. Specifics may be different than your screenshot, as I just picked one of the mindumps that you provided. It got:
PAGE_FAULT_IN_NONPAGED_AREA (50)
Invalid system memory was referenced. This cannot be protected by try-except.
Typically the address is just plain bad or it is pointing at freed memory.
Arguments:
Arg1: ffffef8d5e280008, memory referenced.
Arg2: 0000000000000000, X64: bit 0 set if the fault was due to a not-present PTE.
bit 1 is set if the fault was due to a write, clear if a read.
bit 3 is set if the processor decided the fault was due to a corrupted PTE.
bit 4 is set if the fault was due to attempted execute of a no-execute PTE.
- ARM64: bit 1 is set if the fault was due to a write, clear if a read.
bit 3 is set if the fault was due to attempted execute of a no-execute PTE.
Arg3: fffff8017a1233d0, If non-zero, the instruction address which referenced the bad memory
address.
Arg4: 0000000000000002, (reserved)
The 2 in Arg4 is explained a little more in the web site documentation I cited for this BSOD:
0x2 - NONPAGED_BUGCHECK_NOT_PRESENT_PAGE_TABLE The address referenced does not have a valid active page table entry.
What that means should best be interpreted by a Windows internals expert. I don’t know if the Duplicati C# application developers happen to have such skills. You might need different help.
Sysinternals Process Monitor can look in detail at what Duplicati is doing. During a backup, it examines Source, possibly reading files. It will read and write temporary files. SQLite also will.
tempdir and asynchronous-upload-folder can move them, and Database could also be moved, which (unless it’s something I missed) would leave the Source area as candidate for scanning.
Using Process Monitor for something winding up in BSOD raises the question of whether it can write its information out in a way that will survive the BSOD. I don’t know. It does have ways to change its viewing position, as the view might vary above and below antivirus, due to “altitude”.
The Ultimate Guide to Procmon is a bit old, extensive, and one of many maybe-helpful articles.
EDIT:
Debugging Details:
------------------
*** WARNING: Check Image - Checksum mismatch - Dump: 0x2cb74d, File: 0x2cb743 - C:\ProgramData\Dbg\sym\win32kbase.sys\ABC321FD2d7000\win32kbase.sys
From dir command, it looks like WinDbg downloaded some information for me when I ran it:
Directory of C:\ProgramData\Dbg\sym\win32kbase.sys
02/23/2025 09:17 AM <DIR> .
02/23/2025 09:17 AM <DIR> ..
02/23/2025 09:17 AM <DIR> ABC321FD2d7000