Hey all,
A while back I set up some instances of Duplicati behind Traefik. I used Traefik’s http auth middleware in front of Duplicati to secure them. (This was before there was any password protection.)
This worked for a long time, but a while back something changed and my instances stopped loading my configuration. At the time I didn’t have the time to dig into it, and nothing was super important about the backups, so I just turned them off and didn’t try to figure it out until now.
Duplicati is running in a Docker container as part of a Swarm Stack. As of my testing today, it’s Duplicati - 2.1.0.4_stable_2025-01-31.
Traefik is on 2.11.
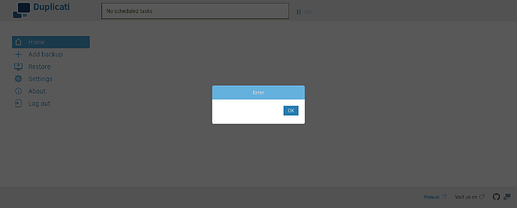
As far as I can tell, if you have the Traefik basic auth middleware enabled for your Duplicati service, after logging in using Duplicati’s UI password, you get a screen like this:
In Firefox’s network inspector, I see a lot of 401 errors.
In the console I see the same errors and can copy them. Here is one:
XHRGET
https://myinstance.mysite.mytld/api/v1/notifications
[HTTP/2 401 101ms]
GET
https://myinstance.mysite.mytld/api/v1/notifications
Status
401
VersionHTTP/2
Transferred176 B (17 B size)
Referrer Policystrict-origin-when-cross-origin
DNS ResolutionSystem
content-length
17
content-type
text/plain
date
Sat, 08 Feb 2025 18:05:17 GMT
www-authenticate
Basic realm="traefik"
X-Firefox-Spdy
h2
Accept
application/json, text/plain, */*
Accept-Encoding
gzip, deflate, br, zstd
Accept-Language
en-US,en;q=0.5
Authorization
Bearer redacted_token
Cache-Control
no-cache
Connection
keep-alive
Cookie
redacted_sessionid; default-theme=ngax
DNT
1
Host
myinstance.mysite.mytld
Pragma
no-cache
Referer
https://myinstance.mysite.mytld/ngax/index.html
Sec-Fetch-Dest
empty
Sec-Fetch-Mode
cors
Sec-Fetch-Site
same-origin
TE
trailers
User-Agent
Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:133.0) Gecko/20100101 Firefox/133.0
Anyway, I’m just curious if anyone has any ideas what is going on. Have both the http auth user/password, and Duplicati’s password would be good. Adds an extra layer of defense. ![]()
One random thought, could the basic auth be messing with the websockets? Traefik supports websockets automatically, but maybe the middleware doesn’t?